Your Rich Uncle an Ocean Away, Debt Collectors, and Other Undesirables
There’s no doubt about it: the Internet has united the world, permitting us almost instantaneous access to the entire sum of human knowledge. Technology like the World Wide Web, social media, and email have made it triflingly easy for phishing emails to hook someone with a couple of keystrokes and a broadband connection.
Unfortunately, it has also afforded con artists and digital pickpockets the ability to solicit the gullible, naïve, and otherwise uninformed for incredible sums of money. When someone sends you an email claiming to be a government representative, a debtor, or the representative of a wealthy relation in another country, you might just be getting phished.
What’s “phishing”? It’s social engineering, and it’s an act of fraud. It’s a way for bad-faith actors to get your username, passwords, and the information they give access to.
What Does a Phishing Email Look Like?
Well, it typically looks something like this:
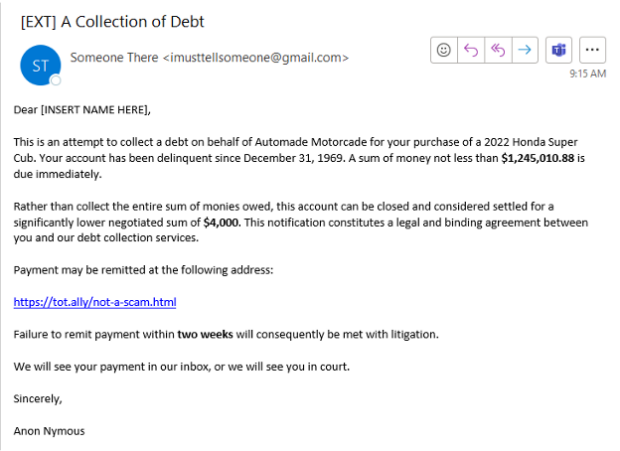
Let’s really break down the elements at play here.
Public Email
Phishing attempts will often use free email services. They do this for several reasons, but mainly, it’s because email con artists and grifters don’t have money to afford a real service—and if they did pay for a service, that’s a paper trail linking them to their identity. Almost no reputable business uses Gmail or other free email services.
Incongruous Information
The alleged debt is for a vehicle released in 2022, with account delinquency occurring in 1969. Unless you have somehow become a time traveler, this inconsistency is a gigantic red flag.
Who are they talking to?
Notice that the phisher in this example doesn’t even give us the dignity of acknowledging our name. Rather, they’re using a form that has apparently malfunctioned: this is typical of phishers who use automated tools for mass mailing the same message to hundreds, maybe thousands, of people. This is one way that systems like Gmail and Office block them: a significant chunk of the verbiage is identified, and then subsequent messages are filtered.
An Exaggerated Threat
Notice how much money this phisher claims we owe? Even with current interest rates, there is no way that an inexpensive vehicle such as the model described would cost that much, even if you paid for fifty years. The purpose of this ludicrous sum of money is to make you afraid. If you saw it and got nervous, it worked. When you’re nervous, your critical thinking takes a backseat to the primal part of your brain that wants to survive.
A “Generous” Compromise
The relatively smaller sum of $4,000 is deliberate. First, it’s an amount that is easier to pay. Second, although large for an individual, $4,000 for a company is not likely to raise any alarms to a payment processor. The phisher has attempted to make you frightened, then feel relieved. You’re smarter than that, and you won’t pay a cent.
What Do You Do with the Phishing Email?
Great question! There are a couple of options. If you received it at your personal address, simply block it and move on. To do this, right-click on the email in your inbox, and you will see the following options (this assumes you’re using Outlook):

After you block the sender, it’s not likely you’ll receive another email from that exact address. But what if you received this in your company email? In that case, the phisher is likely attempting to extort not just you but the people you work with.
Time for Heroics!
Let’s suppose that blocking this would-be extortionist isn’t enough. No, you want to keep your organization safe from this would-be con artist. How do you do that? By utilizing your IT department. You might be tempted to forward the scam email to them. Understandable but not advisable. Rather, we’re going to save the message in a format that lets your IT department get a bit more useful information. We’re going to save the message from your inbox. Here’s how. First, double-click the email in question. You will know you’ve done it right if you see the message open in a new window:

With this open, we’re going to click File:

…and on the subsequent window, click Save As:

This will further prompt us for a location to save. Notice that the file type ends in .msg.

The next step is to submit a helpdesk ticket to your IT department describing what you received and attaching the file you saved for further analysis.
Uh… I sort of… clicked the link…
Mistakes happen. Let’s go to that link and see what kind of web page it takes us to:


We’ve typed in our credentials. Let’s see what happens when we “confirm” our identity:

This “error” is deliberate: it will make you think you can just return. Meanwhile, the information you have submitted has been collected by the phisher. Some phishers don’t even give a false error: the page will simply refresh or go blank, giving you no clue what has happened.
And just like that, we have surrendered to a malevolent actor our account credentials. Now they can see our Netflix, our Hulu, our 401(k), our everything. Any service or website you used this email to sign up for is a potential vector for further attack.
What Do I Do Now!?
As soon as you have become aware that you might have had your account information compromised from a phishing email, you should change your passwords to something complex. Here are some examples of bad passwords:
Helix@123
P@ssw0rd
0pen$esame
YourKidsName2002
These are terrible passwords and can be brute-forced with minimal effort. Good, strong passwords are long, complex, and contain no dictionary words. Example of good passwords are below:
dhJK&(*#$s32
16!%oifg8#@$
jg9*^jgGF73$5
kshjgo3oi345%#@$^Tlksdgfsdgl;ja034098@#)#(%089SEGTJ0#$)*U9SWGU3W459#$()*%
These are incomprehensible, sure, but that’s why they are safe.
Never Going to Remember These Complex Passwords?
Who said you had to? There are many password management applications that operate off a single master password or an authentication key, which ensures you don’t have to remember anything at all. Common password management software includes any of the following: 1Password, LastPass, Dashlane, and KeePass. Which of these you use is up to you, but all of them will help to keep your passwords safe, stored somewhere you can easily access. And, most importantly—safe from phishers.
How to Protect Yourself from Phishing Emails
Now you know what phishing emails look like and how to protect yourself (and your organization) against them. You know you should use complex passwords and manage them with appropriate software. But what if there were more you could do? What if you could hire a team of people to manage your logins so that if your password is compromised and you don’t know it, someone on the alert still would?
That’s where we come in. IT Acceleration utilizes the latest technology for monitoring login information across the globe. If someone with an IP address in the Russian Federation uses your username and password to log into a system we manage, we’ll know. If you’re sitting safely at home in New York, and logging into your work email in Moscow, we can guarantee you that we will notice, and take appropriate preventative measures to safeguard your account, your data, and everything related .
More, we can do this on the scope of your entire organization. That’s us, and that’s what we do: keep safe from them what’s precious to you.
If you’d like to learn more about protection yourself and your organization from phishing emails and other fraudulant activity, contact us today.
Stay safe!
